When Using Kerberos Authentication Which of the Following Terms
Passwords are never sent across the network because only keys are sent in an encrypted form. -The Service Principal Name SPN for the remote computer name and port does not exist.
Kerberos Authentication Documentation For Bmc Atrium Single Sign On 8 1 Bmc Documentation
Hashkey Voucher Coupon Ticket You want to use Kerberos to protect LDAP authentication.
. -Kerberos accepts domain user names but not local user names. When using Kerberos authentication which of the following terms is used to from COMPUTER S 546 at University of Leeds. - Routers send routing information only to their neighbor routers.
Which authentication mode should you choose. The entire routing table is sent to other routers. View all Category Popup.
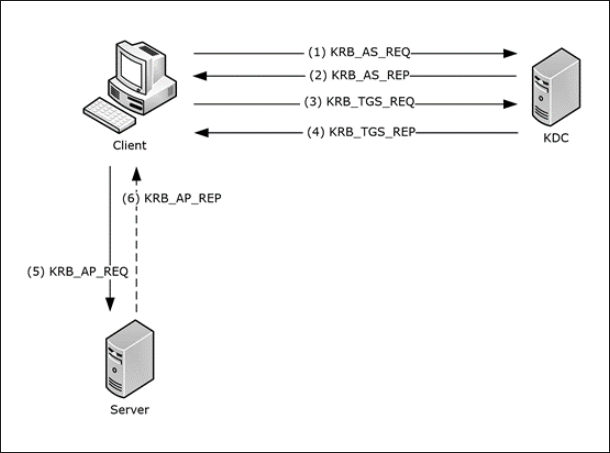
WinRM cannot process the request. In classic Kerberos users share a secret password with a Key Distribution Center KDC. Authentication is mutual so client and server authenticate at the same steps and they are both sure they are communicating with the right counterpart.
I am building a login portal based on IdentityServer so what I am wanting to do is to automatically detect the user being kerberos enabled when they get directed to the login page from an application - but the thing is I need the internal users to stop. Gss_kex is optional to authenticate the server using Kerberos as well rather than its SSH key. Support for it paramiko has been committed in 092014 in pull request 267 and is available from v115 onwards.
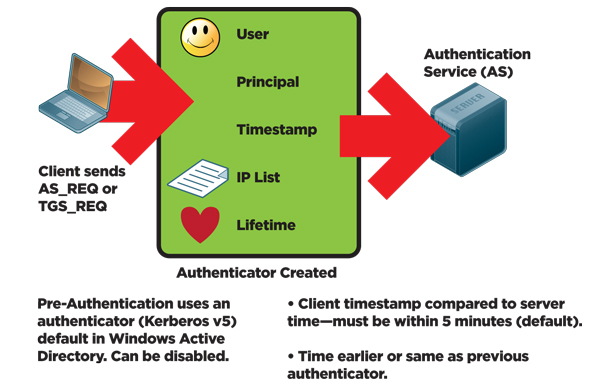
When using Kerberos authentication which of the following terms is used to describe the token that verifies the users identity to the target system. The Kerberos principal name that the. Use gss_auth parameter of SSHClientconnect.
Forums Selected forums Clear. -Kerberos is used when no authentication method and no user name are specified. To use it See Installing docs for additional requirements.
The following error occurred while using Kerberos authentication cannot find the computer. Ticket You are a contractor that has agreed to implement a new remote access solution based on a Windows Server 2016 system for a client. The client sends an authentication request to the authentication server.
Kerberos works as follows. -Kerberos is used when no authentication method and no user name are specified. Which of the following are required when implementing Kerberos for.
Terms in this set 15 When using Kerberos authentication which of the following terms is used to describe the token that verifies the users identity to the target system. -Kerberos accepts domain user names but not local user names. NIST SP 800-95 from IETF RFC 1501 A widely used authentication protocol developed at MIT.
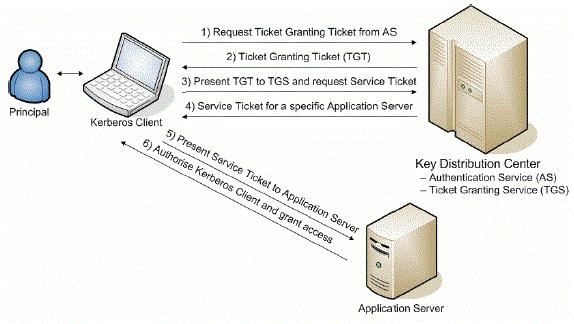
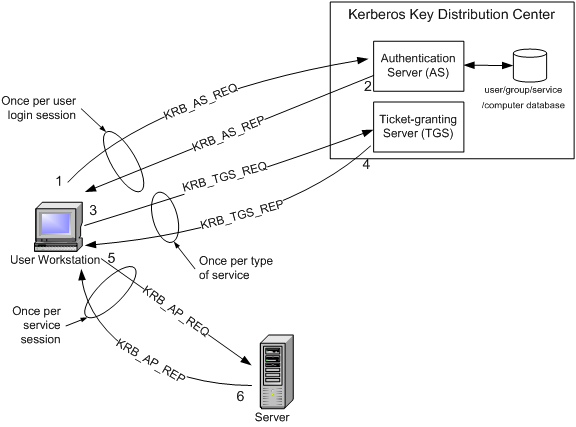
The authentication server validates the user identity and grants a ticket granting ticket TGT. 8 When using Kerberos authentication which of the following terms is used to from EET 252 at ECPI University Virginia Beach. When using Kerberos authentication which of the following terms is used to describe the token that verifies the identity of the user to the target system.
The authentication server validates the user identity and grants a ticket granting ticket TGT. Kerberos a network authentication protocol included in the Microsoft Windows operating systems can be used in conjunction with Security Support Provider Interface SSPI to provide pass-through authentication with secret key. 6109 Section Quiz When using Kerberos authentication which of the following terms is used to describe the token that verifies the users identity to the target system.
Which of the following authentication methods uses tickets to provide single sign-on. -The Service Principal Name SPN for the remote computer name and port does not exist. The TGT validates the user identity and is good for a specific ticket granting server.
Internal users should be able to use SSO rather than having to input a password but external users cannot use SSO. Kerberos works as follows. The Kerberos support of Directory Server provides support for the GSSAPI SASL mechanism.
This enables both Directory Server and Windows 2000 LDAP clients to use Kerberos authentication with the Directory Server. When using Kerberos authentication which of the following terms is used to describe the token that verifies the identity of the user to the target system. To enable Kerberos authentication you must have the network authentication service configured.
Resources for IT Professionals. The principal advantages in adopting Kerberos as an authentication service are. Kerberos uses a trust broker model and symmetric cryptography to provide authentication and authorization of users and systems on the network.
When using Kerberos authentication which of the following terms is used to describe the token. The TGT validates the user identity and is good for a specific ticket granting server. The client sends an authentication request to the authentication server.

Kerberos Important Changes Starwind Blog

Kerberos Authentication Axway Documentation

Kerberos Authentication Documentation For Bmc Atrium Single Sign On 9 0 Bmc Documentation

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
Intel Amt Sdk Implementation And Reference Guide
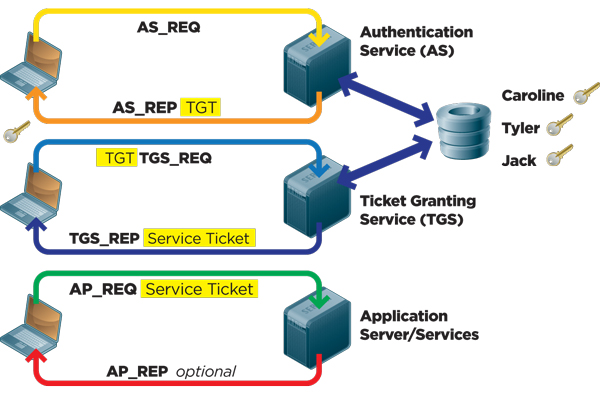
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
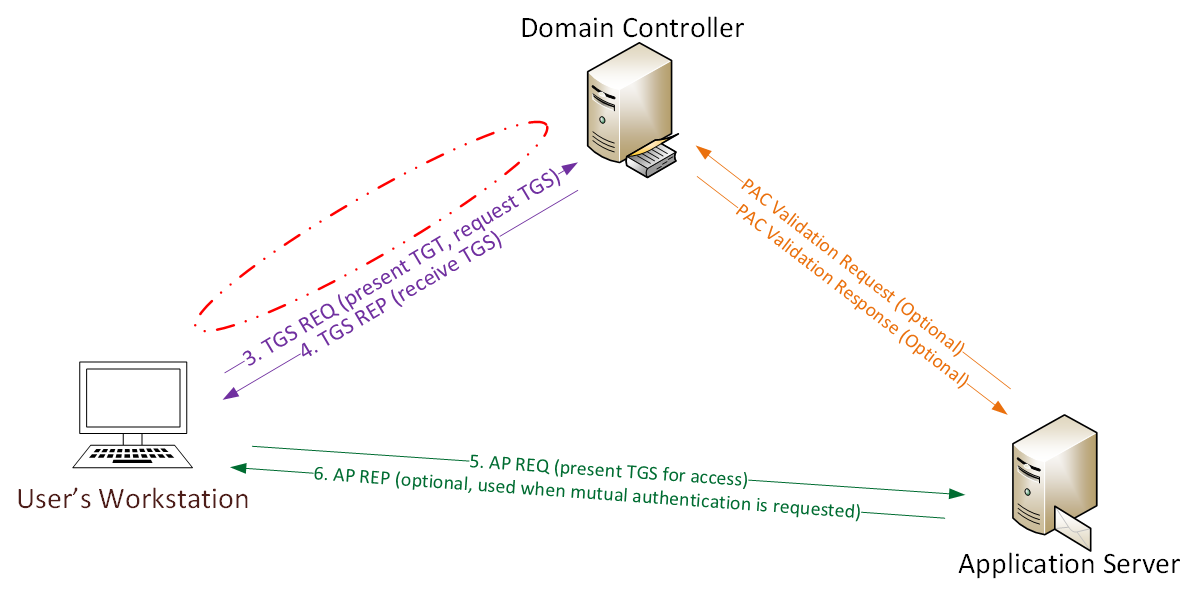
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security

Using External Kerberos Authentication With Amazon Rds For Postgresql Aws Database Blog
Integrated Windows Authentication Iwa With Kerberos And Wso2 Identity Server By Farasath Ahamed Identity Beyond Borders Medium

Kerberos Part 1 How It Works Acc3ssp0int
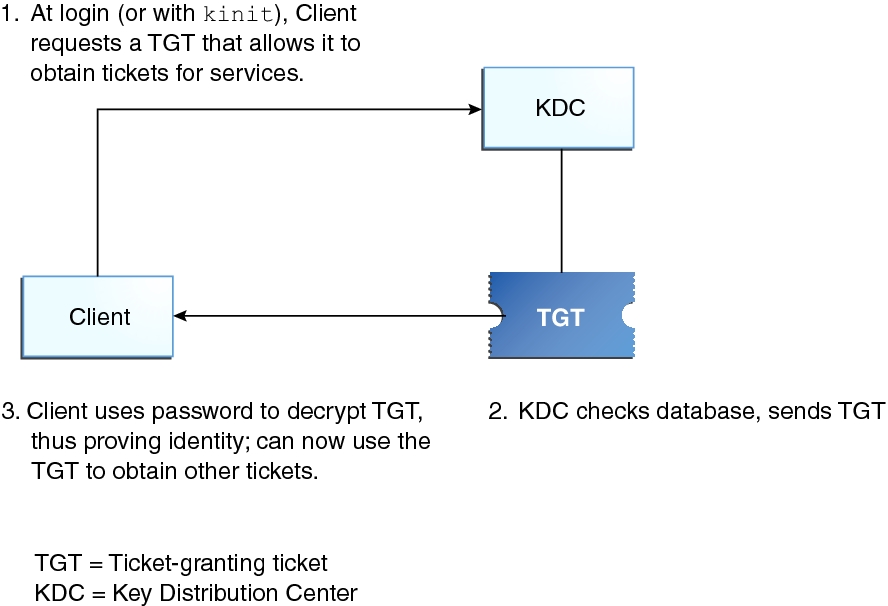
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3
How Does Kerberos Authentication Work Quora
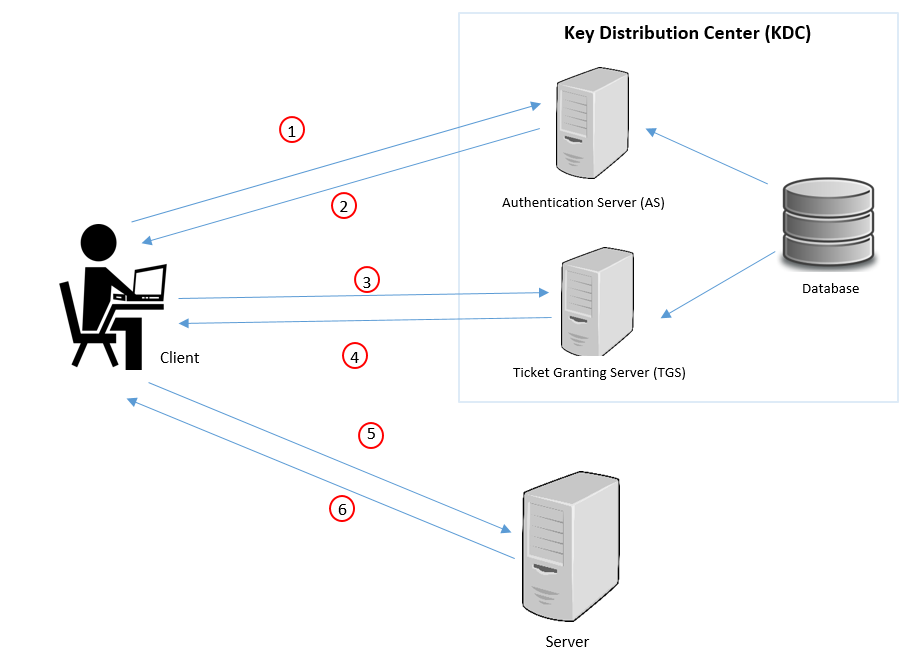
Kerberos The Computer Network Authentication Protocol By Dewni Weeraman Medium

Kerberos Authentication Protocol Download Scientific Diagram
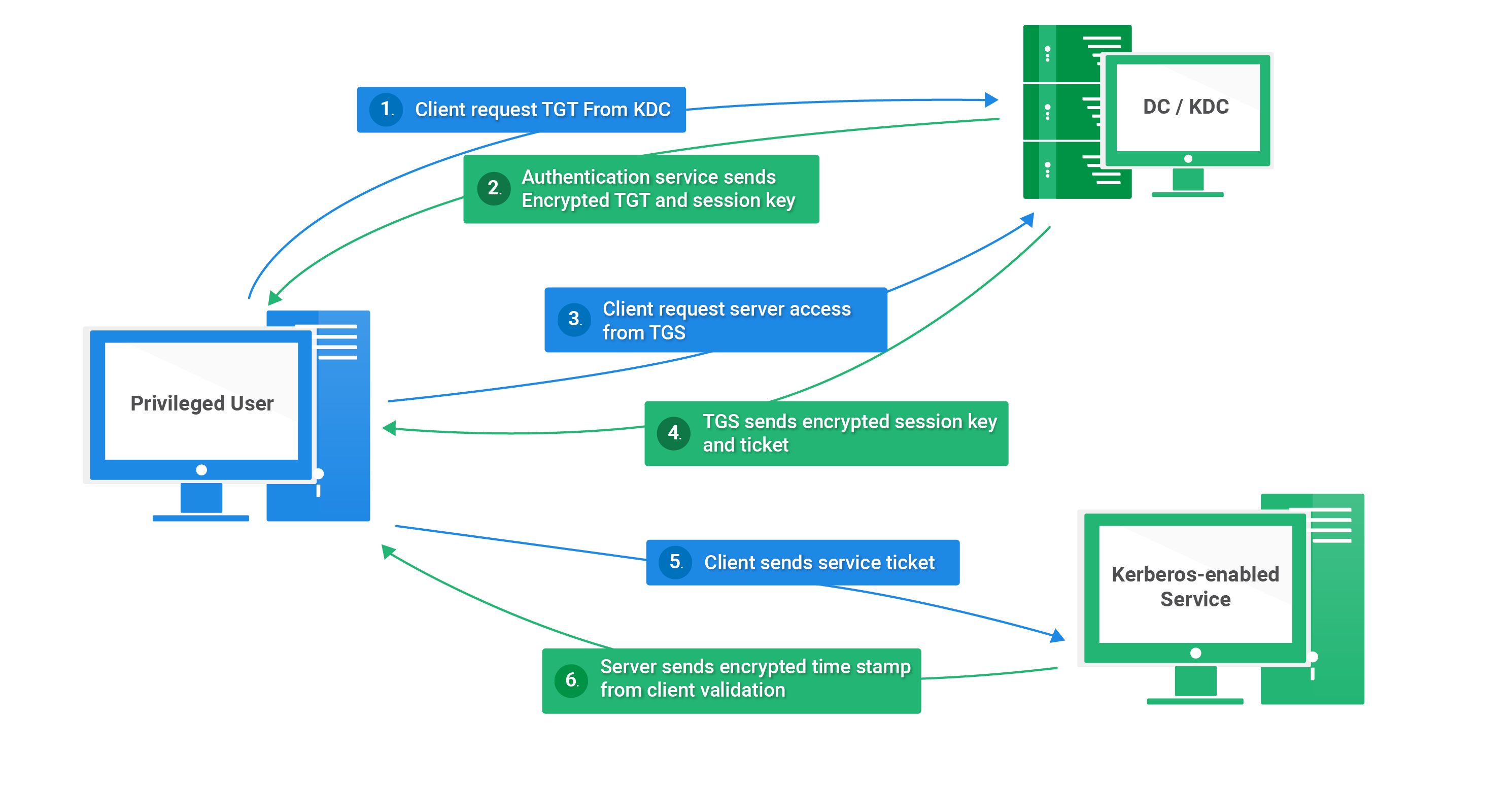
Kerberos Fundamentals What It Is And How It Works Qomplx

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
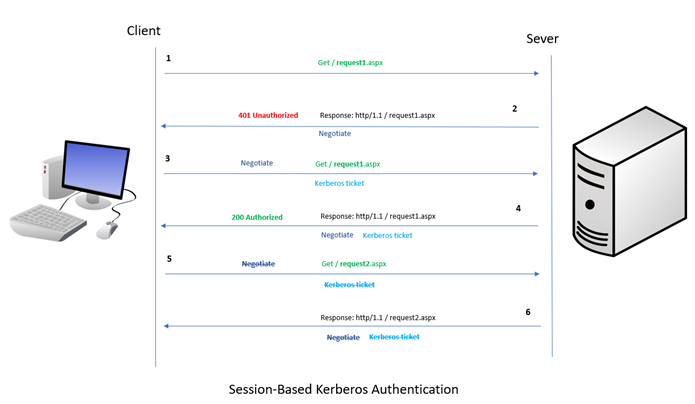
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community

Comments
Post a Comment